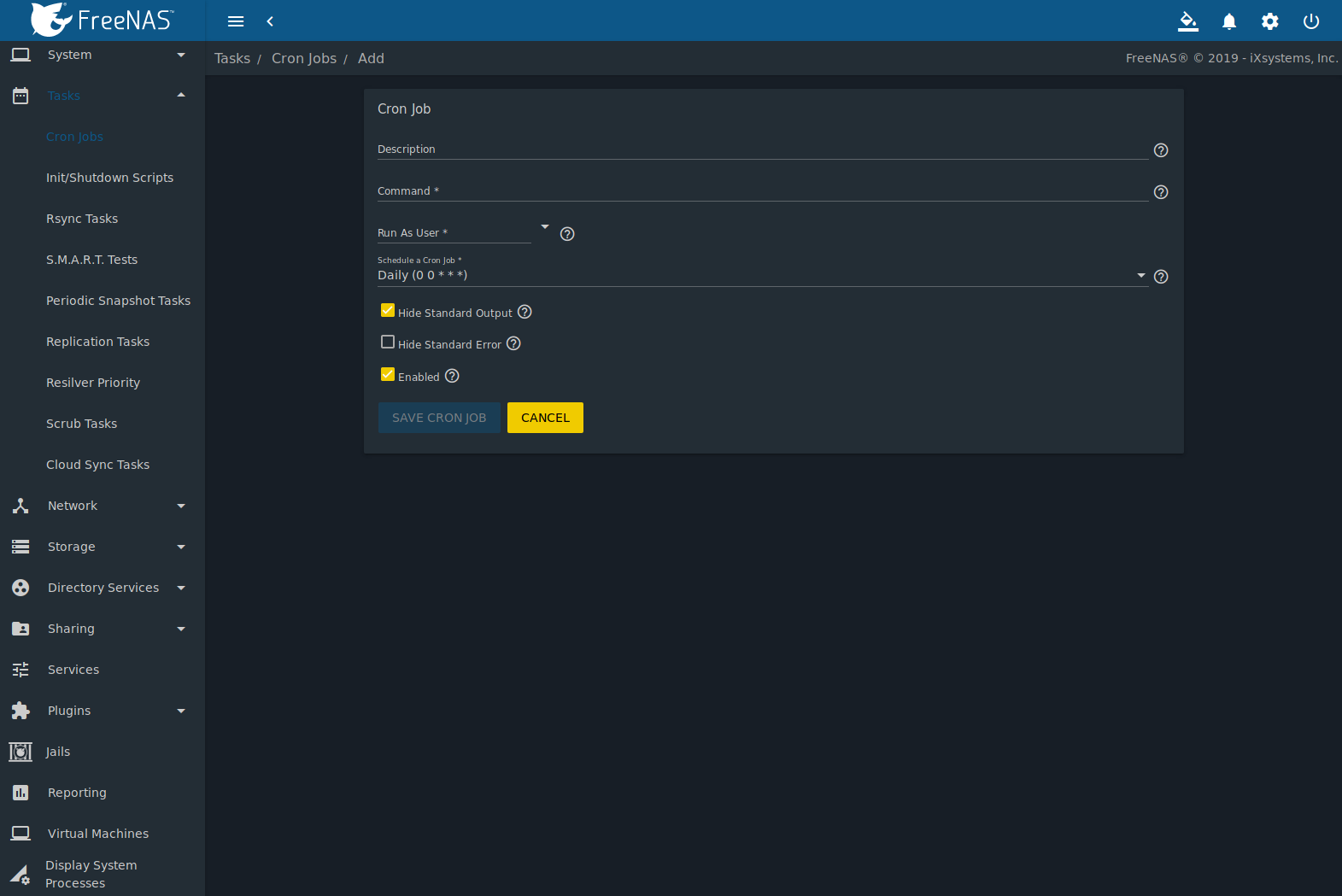
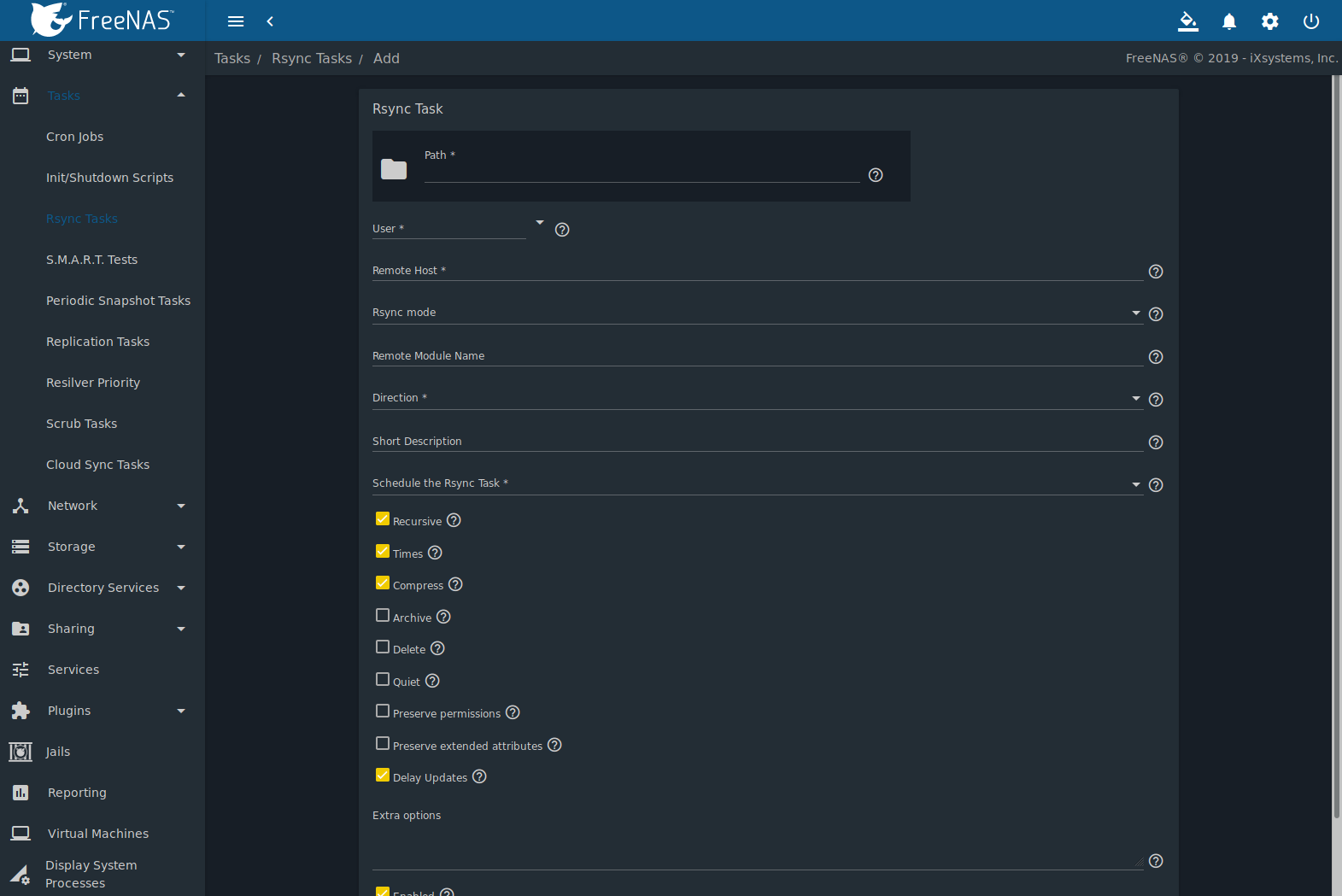
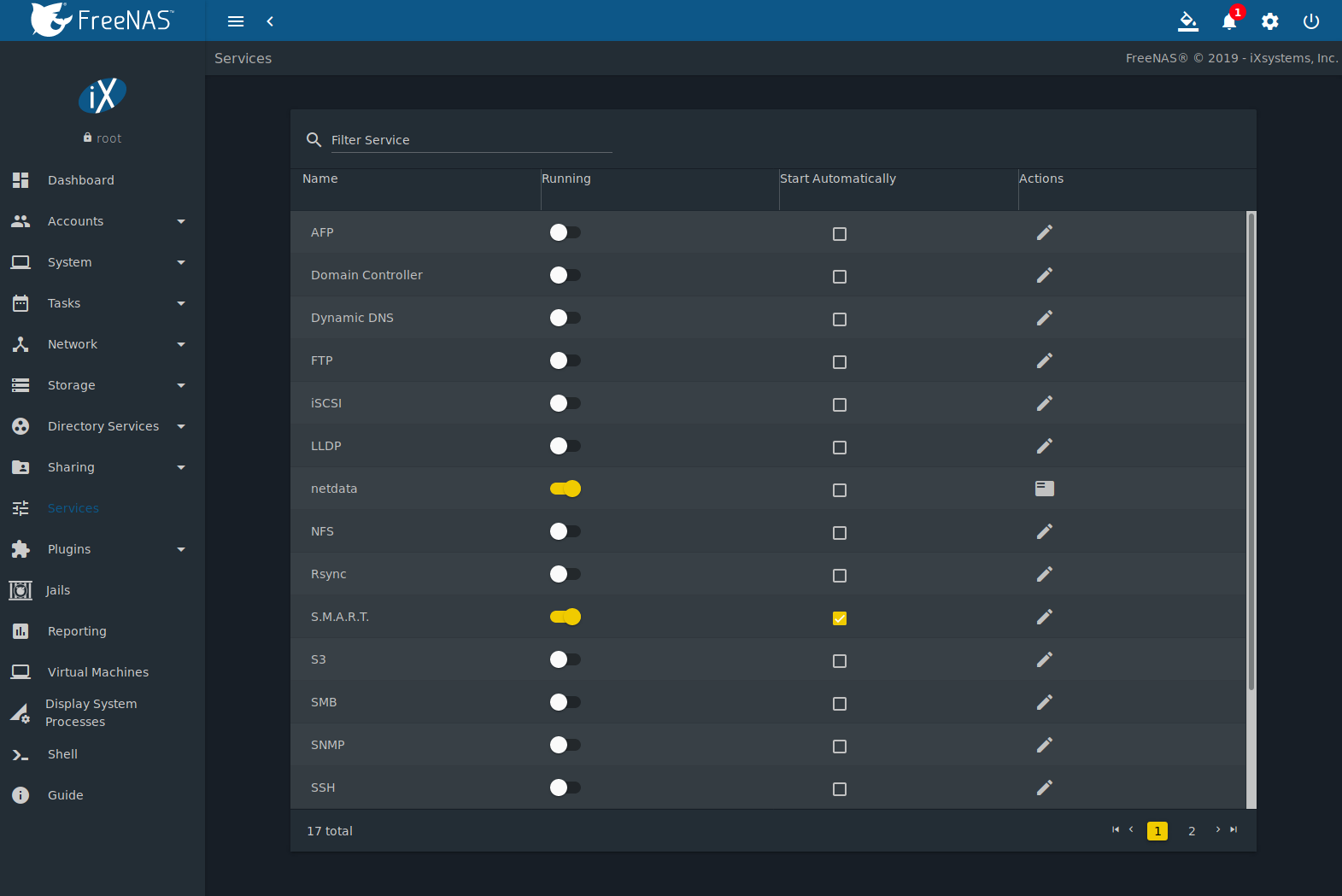
freenas lcd module quotation
For all this time freenas =never= let me down. My data survived hdd crashes, MB crashes, PSU crashes and countles power line failures etc. Once my server was almost flooded, and once water from broken water pipe was pouring over freenas box - it was standing 1 cm deep into water and box completely wet ;-) And my data was intact!
I am using RP and dsm7.1 on a branded nas box (wd pr4100) with an lcd display. The folks using freenas/truenas have worked out a script to load on boot that allows you to read a multitude of info from this screen..cpu temp, ip, etc. Is there a way to make (which is for truenas/freenas) work on a RP 7.1-42661 apollolake build?
Generally, the FreeNAS boot device is an open-source Network-Attached Storage (NAS) operating system based on FreeBSD. So far, it has helped several people convert their old computer systems to their personal cloud drive/NAS. During its set-up, you can try it on a Virtual machine before its installation to the main server or system. Additionally, you can install FreeNAS on aUSB drive or a blank pen drive, as we’ll discuss today. But first, create a FreeNAS bootable USB drive.
The first step involves downloading a FreeNAS OS image (in the form of a .iso file) into your USB drive. There are several FreeNAS in the market, but we’ve settled for FreeNAS 11.3 in this project.
Now, you’re free to create your root password that’ll later help you log into the FreeNAS while in the Web Interface. Once the installation process is over, it should appear like the picture below.
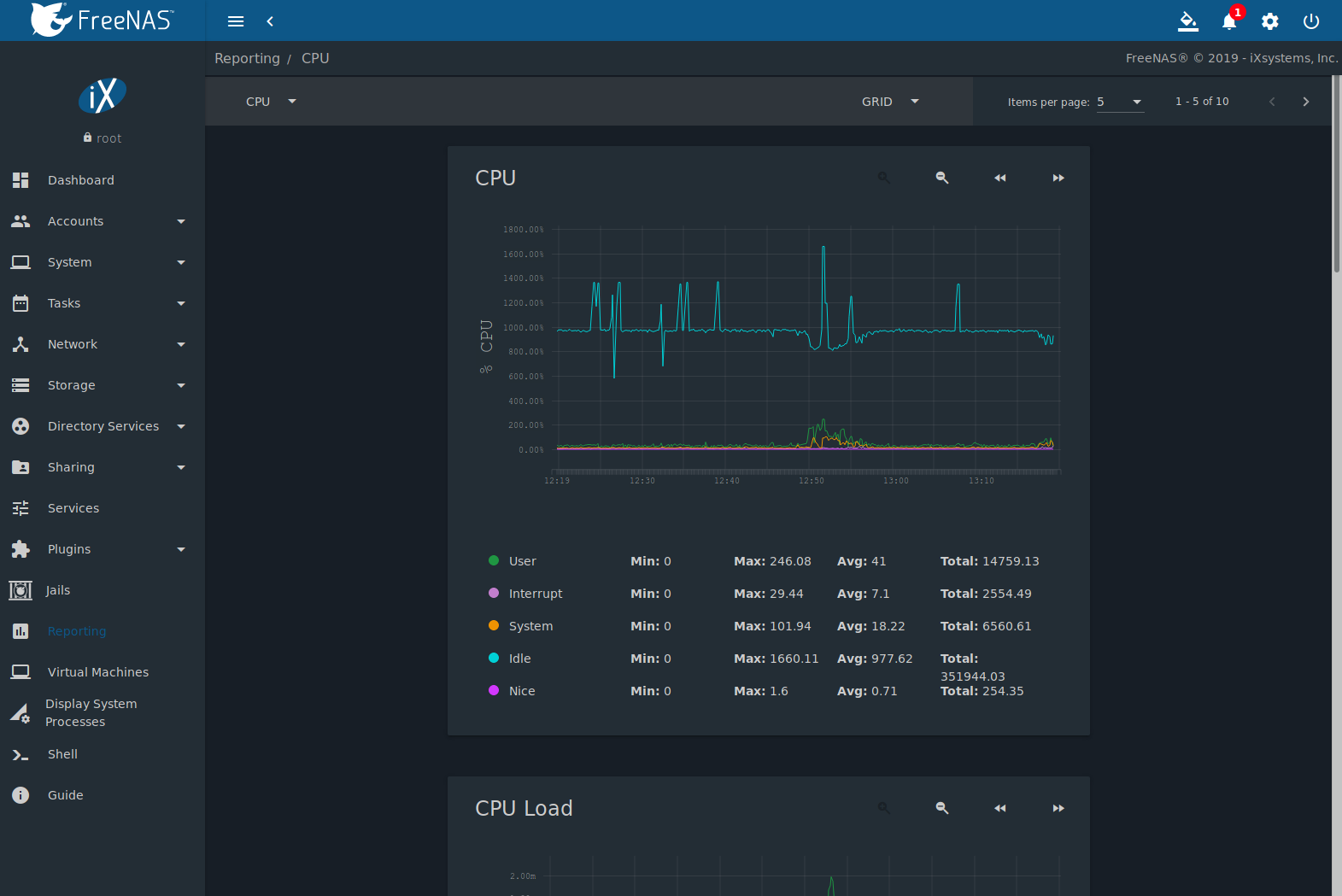
The system doesn’t also support an upgrade on 32-bit hardware. You can upgrade the system if the hardware supports 64-bit and 32-bit versions of FreeNAS®. Unfortunately, you’ll lose archived reporting graphs when upgrading.
That’s it for today, installing a FreeNAS on a USB device and having a personal NAS. It is a simple process with minimum requirements. If you have questions, you can contact us. We’ll be glad to help.
This is the beauty of FreeNAS. If you"re a company that prefers to be hands-on, can self-support, and you don"t need HA, then FreeNAS can be a perfect fit. You can install it on the hardware of your choice and you don"t owe us a dime. And, FreeNAS does have an HCL, by the way (it"s effectively the FreeBSD HCL -- our FreeNAS versions are in sync with the FreeBSD version to make things easy)
If your company hits the scale where being so hands-on isn"t sustainable, or if you decide you need HA or support because the data is critical, then that"s where TrueNAS systems come in. TrueNAS is also fully compatible with FreeNAS, so you can use them to replicate to one another if you see fit.
Is it really the case for python, that you have to install each module per request from an executed program? Or is there a way to determine which module the 3rd party program needs and install it in upfront?

The Displaytech 204G series is a lineup of 20x4 character LCD modules. These modules have a 98x60 mm outer dimension with 77x25.2 mm viewing area on the display. The 204G 20x4 LCD displays are available in STN or FSTN LCD modes with or without an LED backlight. The backlight color options include yellow green, white, blue, pure green, or amber color. Get a free quote direct from Displaytech for a 20x4 character LCD display from the 204G series.
If the computer that you are logging into isn"t hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting (y/n) y
Let’s go ahead and add two factor authentication to SSH. There are several things we need to do to get that accomplished. The quick overview: 1. Make some config changes to sshd_config, some easy, some not so much 2. Tell PAM about the Google Authenticator module and how we want to use it. 3. Your homework is applying the concepts from my post on getting hacks to survive upgrades. Before we do any of that, we need to decide how we want to implement this. In my mind, it makes sense to initially allow users to login to ssh with a public key and either a Google Authenticator code or their user password. This will allow some time for everyone to get set up without any of them getting locked out. Eventually, I’ll probably switch it to require a public key and just the Google Authenticator code. The decision we make here affects how we set the sshd_config parameter AuthenticationMethods, as well as how we configure /etc/pam.d/sshd. For a more in-depth explanation of the options that AuthenticationMethods offers, please see: http://lwn.net/Articles/544640/ For a full explanation of setting up the PAM module in /etc/pm.d/sshd, please see: FreeBSD Man Pages I’ll show you how I have mine set up.
Note that the atime value is set to off, which is different from the default. From the FreeNAS User Guide, disabling atime prevents the production of log traffic while files are being read, and results in significant performance gains, which is desirable for our data folder.
Now it’s time to create the jail. This can be done with the web UI, however I prefer to use the command line interface, and so the rest of these instructions will be presented there. This guide, will therefore present the instructions for the command line interface. First, you’ll need to SSH into your FreeNAS host. Instructions on how to configure SSH are available here. The gist of this is that you’ll need to enable the SSH service in the FreeNAS UI and configure the public/private key pair for your user, and then make a connection. From a unix terminal (macOS, Linux), this will look like the following, assuming a FreeNAS host local IP of 192.168.0.9:
To provide some insight as to what this is doing; the -n flag allows the specification of the jail name, in this case “nextcloud”, the -r flag specifies the release of FreeBSD to be installed in the jail (Note that this version must be the same or lower than your version of FreeNAS. For example, If your FreeNAS version is 11.1, then you would need to pass 11.1-RELEASE as a parameter instead of 11.3-RELEASE; using 11.3-RELEASE would break the jail due to differences in the respective kernels), ip4_addr is the networking specification – in this case the IP/Mask for the jail (192.168.0.10/24), and the interface to use, vnet0. Set this IP value to something convenient to you on the subnet you wish it to be on – the selection is arbitrary, though if you’re new to this, it is advisable for simplicity that you choose an IP on the same subnet as your router. To illustrate this, if your router is 192.168.0.1, then choose an IP of the form 192.168.0.x, where x is a number between 0 and 254. The defaultrouter parameter specifies the router for your network; typically this will be 192.168.0.1 by default, but if it’s something else put that here. vnet=“on” enables the vnet interface, which is required as we previously specified vnet0 as the interface. allow_raw_sockets=“1” enables raw sockets, which enables the use of functions such as ping and traceroute within the jail, and enables interaction with various network subsystems. boot=“on” enables the jail to be auto-started at boot time. More detail on all of the parameters that can be used to configure a jail on creation can be found in the man page for iocage. If the jail doesn’t start automatically after issuing this command, start it manually:
where source_location is the dataset location on your FreeNAS host, and destination_location is the mount location within the jail. rw/ro refers to the permissions the jail has for the mounted dataset; rw is read/write and ro is read only. Choose ro if the jail needs to read the data but shouldn’t be able to alter it. Obviously, in the case of Nextcloud, we want to give all of these mounts read write access. The -a flag is to add an item to the jails fstab file. The -e flag can be used to edit an entry once made:
MariaDB is now configured. At this stage, the installer should have created a user named ‘mysql’, and a group named ‘mysql’ within the jail, with UID=88 and GID=88 respectively. You’ll recall earlier in the guide, we created a mysql user and group with these UID and GID. It is imperative that the UID and GID of the user and group created earlier on the FreeNAS host, and the user and group created during the mysql installation within the jail match. If they don’t, you will run into permission issues, so go ahead and change the ID of the user and group on the FreeNAS host if this is the case for you.
The next directive,
Nextcloud recommends a number of steps be taken to harden your server: 1. Give PHP read access to /dev/urandom 2. Enable hardening modules 3. Place data directory outside of the web root 4. Disable preview image generation 5. Use HTTPS 6. Redirect all unencrypted traffic to HTTPS 7. Enable HTTP Strict Transport Security (HSTS) 8. Use proper SSL configuration 9. Use a dedicated domain for Nextcloud 10. Ensure that your Nextcloud instance is installed in a DMZ 11. Serve security related headers by the Web server
The Nextcloud documentation recommends the use of hardening modules such as SELinux. SELinux (Security-Enhanced Linux) is a Linux kernel security module, that provides a mechanism for supporting access control security policies, including mandatory access controls. FreeBSD is obviously not Linux, and so does not include the SELinux modules. However, it does have it’s own system called Mandatory Access Control. This allows an administrator to ensure that a user will not be permitted to change security attributes at will. All user utilities, programs and scripts are required to work within the constraints of the access rules provided by the selected security policy modules. The Nextcloud Documentation provides some configuration advice for SELinux, namely:
There are a number of system hardening modules that FreeBSD offers at install time. Unfortunately, since this is a jail, we were not presented with these options. The options are as follows:
In essence, this is a process that doesn’t provide any additional security to your Nextcloud instance directly. In general, it would, however, provide a second line of defence to prevent access to the rest of your LAN if the Nextcloud instance is compromised. In the case of running Nextcloud in a FreeNAS jail, the efficacy of this is in question. According to iXsystems, the entire LAN accessible to the FreeNAS host would be routable by a compromised jail, making this segregation of jail from host an exercise in futility.
Now, if you’re self hosting, and you have a residential internet plan with your ISP, your IP address is likely not static. If it is static, you can disregard this. What this means is that your ISP may periodically change your public IP. This can be problematic if you’re hosting a web server, as the DNS Servers will not update as your IP changes, breaking the link to your web server. To address this, there are two alternatives. The first is to use a Dynamic DNS (DDNS) service and use either the FreeNAS DDNS service or your router to keep it updated, or update the DNS servers directly. Free examples of DDNS providers include No-IP, Free DNS and Easy DNS, which may also provide you with a domain – I know that No-IP does. In lieu of buying domain name, the domain provided by the DDNS provider will be sufficient, and this applies to the entirety of the previous instructions that have dealt with domain names. If you already own a domain name that you want to use, you just need to add a CNAME record for the DDNS domain to the DNS record for your domain. As an example, if your DDNS domain is cloud.no-IP.org, you would add a record pointing from cloud.mydomain.com to cloud.no-IP.org. Since this is very specific to each users configuration and registrar etc., I won’t address any more here.
We came to Phoenix Display with a design concept for a new way to utilize an LCD module. After a few discussions with their design team, we quickly learned why our design was not feasible, and could not be manufactured. Within only few days, the Phoenix Display team came up with a better way of accomplishing our objective, and then followed up by developing this LCD display concept for us. Product development processes are typically stressful undertakings, but PDI made it much easier and didn’t give up until they had developed the ideal solution for our new project.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey