128X64 Graphic LCD - 128x64 lcd
Function: The primary function of a firewall is to monitor and manage traffic according to pre-established security rules, preventing unauthorized access. An IDS identifies and alerts administrators of potential threats without taking direct action. In contrast, an IPS actively blocks malicious traffic, providing proactive defense.
16:10aspect ratio
For instance, the FS NSG-5220 next-generation firewall designed to offer robust security features and high performance. Equipped with a rich selection of ports and boasting impressive speeds such as 20 Gbps Firewall Throughput and 5.5 Gbps NGFW Throughput. This firewall series not only ensures high security performance but also supports comprehensive advanced threat detection and prevention.
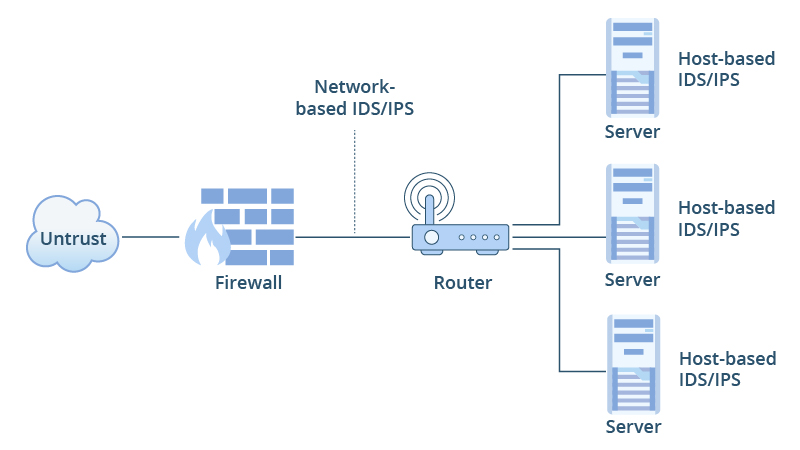
Product application: The intrusion detection system must be installed at the network center and have the ability to monitor all network traffic to fulfill the goal of fully detecting cyber security status. To control the security status of the entire information system, distributed deployment—deploying an intrusion detection analysis engine for each subnet and unifying the engine's policy management and event analysis must be implemented if the information system is made up of several logically isolated subnets.
4:3aspect ratio
2022919 — HD group. SCREEN North America Holdings, Inc. 150 Innovation Drive - Ste A, Elk Grove Village, IL 60007, U.S.A.. Tel: +1-847-870-7400
Traffic Filtering: A firewall filters traffic based on pre-established rules without analyzing traffic patterns. An IDS examines traffic behavior to detect malicious patterns and generates alerts. An IPS also examines traffic behavior but takes additional steps to block malicious traffic.
5:4aspect ratio
Performance Impact: A firewall generally has minimal impact on network performance since it uses simple rules to filter traffic. An IDS can significantly impact performance depending on the complexity of its traffic analysis and the volume of alerts. An IPS may substantially affect performance due to real-time traffic analysis and active threat mitigation.
Considering the above two points, enterprises can choose different intrusion prevention products according to their defense needs to bring better security protection to enterprise cyber security.

Working Principle: A firewall filters traffic based on IP addresses and port numbers, acting as a barrier between trusted and untrusted networks using predefined security rules. An Intrusion Detection System (IDS) monitors real-time traffic for attack patterns, generating alerts when suspicious activity is detected. An Intrusion Prevention System (IPS) not only detects these threats but also actively blocks them by analyzing real-time traffic for known patterns or anomalies.
Product catalogue and online ordering system for Digital Industries and Smart Infrastructure. Home · Deutsch.
Lattice ECP5-5G Versa Kit on sale for $99 ... The ECP5™ Versa Development Board allows designers to investigate and experiment with the features of the ECP5 Field ...
Screensize calculator
Small Gaming Desks · Gaming Peripherals. Back; Gaming Peripherals (View All) ... Monitor Accessories. Back; Monitor Accessories (View All) · Monitor Stands ...
It is essential to comprehend the distinctions between firewalls and IDS/IPS to put a robust cyber security plan into action. Firewalls serve as barriers to stop unauthorized users from accessing networks, whereas IDS/IPS monitors network activity to give a deeper examination and identification of possible security concerns. To improve company cyber security, this article should be able to assist you in selecting various intrusion prevention solutions based on your specific needs.
16:9aspect ratioresolutions
1. Someone who's so afraid to lose a bet that they have to be coddled and convinced for an hour that they're going to have a great time and probably win.
Jun 28, 2024 — Screen resolution defines the sharpness and detail of your screen. Resolution can also be understood as a collection of pixels that make an image.
1920x1080aspect ratio
2024726 — Fix 1: Check if It Is a Widespread Issue and Contact the Device Manufacturer. If the issue of lines appearing on the display is widespread, the manufacturer ...
An intrusion prevention system (IPS) is a security tool that actively monitors and analyzes network traffic to identify and block potential threats. Positioned inline with network traffic, typically just beyond the firewall, an IPS can take immediate action by blocking harmful data packets, alerting administrators, or severing connections. It uses various detection methods such as signature-based, anomaly-based, and policy-based detection to protect the network. Unlike an IDS, which only detects and reports threats, an IPS prevents them, offering a more advanced level of security.
Location: A firewall is typically placed at the network perimeter, serving as the first line of defense against external threats. An IDS is usually located within the internal network to monitor traffic without interfering with data flow. An IPS can be deployed anywhere in the network but is often positioned just beyond the firewall to block threats in real-time.
An intrusion detection system (IDS) is a cybersecurity tool or software designed to monitor network or system activities for malicious actions or policy violations. It identifies potential security threats by analyzing network traffic and system behavior, looking for anomalies or patterns indicative of unauthorized access or attacks. When a potential threat is detected, the IDS alerts administrators, allowing them to take appropriate measures to protect the network.
Product value: The monitoring of cyber security status is the main objective of intrusion detection systems. The management of incursion behavior is the main goal of an intrusion prevention system. Intrusion prevention systems can implement deep defense security strategies, which allows them to detect and prevent attacks at the application layer. This is something that firewalls and intrusion detection products are unable to do. In contrast, intrusion prevention systems can implement security strategies.
When and how to select intrusion protection solutions among the three defense options? Two viewpoints are examined in the analysis that follows:
The aspect ratio of a LCD display is the proportional relationship of its width compared to its height. The two numbers are commonly separated by a colon. The most common aspect ratios are 16:9 (aka widescreen) and 4:3 (closer to the shape of a square monitor, such as old CRT’s and TV’s). It is best to choose a monitor with the same aspect ratio as your video signal. You cannot customize a monitor’s native aspect ratio, so it is critical to know the aspect ratio of your incoming video signal beforehand. Use this handy screen ratio calculator to determine what you need.
This sleek monitor has a three-sided ultrathin bezel, small base, and an improved, easy-to-use cable management system.
16:9aspect ratio
The primary distinction between firewalls, IDS, and IPS lies in their roles and actions regarding network security. An IDS/IPS detects and notifies a system administrator of an attack or, depending on its configuration, stops it, while firewalls perform actions such as blocking and filtering traffic.

Screen aspect ratio chartlaptop
To keep their network secure and guard against threats, most corporate networks employ a variety of networking tools and techniques. Among the most crucial defenses are firewalls and IDS/IPS systems. In this article, we will explore these three defenses in detail, highlighting their functions and differences.
An EMI shielding gasket is a mechanical device that helps protect electronics from electromagnetic interference. Traditionally, EMI shielding has been ...
24 May 2021 — Thin film transistor (TFT) is a LCD flat-panel display screen. Learn about TFT's transistors & resolution here.
A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on predefined security rules. Installed at the network's perimeter, firewalls serve as the first line of defense, ensuring that all data packets pass through them before entering or leaving the network. Their primary function is to prevent unauthorized access by evaluating data packets based on criteria such as IP addresses and port numbers. Firewalls analyze these packets and decide whether to allow, deny, or reject them according to the established rules. This process helps to protect the network from external threats and unauthorized access.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey