f5 ltm lcd panel quotation

The liquid crystal display, or LCD panel, provides the ability to control theunit without attaching a serial or network cable. The following menus are available on the LCD panel.
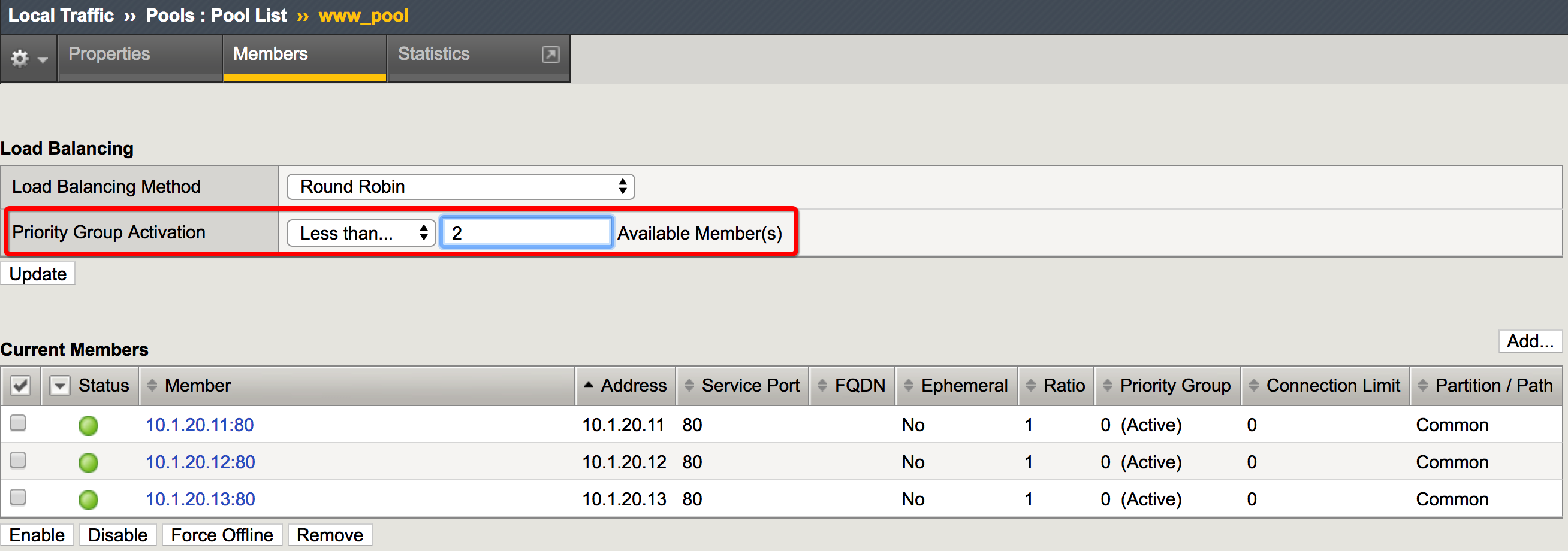
Normally, the screens cycle on the LCD panel at a constant rate. However,press the Check button to toggle the LCD panel between Hold and Rotate modes. In Hold mode, a single screen is displayed. The Rotate mode changes the screen displayed on the LCD panel every four seconds.
Pressing theX button puts the LCD panel in Menu mode. The buttons Left Arrow, Right Arrow, Up Arrow, and Down Arrow are functional only when the LCD panel is in Menu mode.
After you put the LCD panel in menu mode, use the Left Arrow, RightArrow, Up Arrow, and Down Arrow buttons to select menu options. There are four menu options:
You can use the Information menu to access help pages about using theLCD panel functionality. You can also find more information on what different LED activity means, and on the failover state of the unit in a redundant system. Table 3.1 shows the options available on the Information menu.
Use the Check button to turn on (checked) or off(cleared) the heartbeat displayed on the LCD screen. This heartbeat displays if the SCCP is running on the system. This heartbeat does not affect the failover mechanism of the system.
This setting controls the brightness of the LCD panelwhen the backlight is off. Use the Left and Right arrow keys to set the brightness of the LCD panel.
Alertd is the alert daemon which generates the LCD warnings and/or SNMP traps for specific alerts. syslog-ng is the daemon that writes messages to log files and sends messages to alertd for processing. Generally, whatever syslog sends to alertd is also sent to a log file.
I was wondering if it was possible to find out what event triggered the led state from an SSH session rather than emailing the Datacentre, waiting for an Operator to get to the BigIP and relay the LCD message. Note, the operators know nothing about how to navigate the LCD, and there are many operators, so its likely you get a different one each time (plus the attrition rate is high).
Can you click any of the buttons on the LCD and get a response? As Nathan suggested, you should be able to clear the past messages by clicking the check mark button a few times. If not, I"d try logging into the unit and check the recently modified /var/log/ log files, particularly /var/log/ltm, for errors.
Note: You can use Boolean operators (AND, OR, NOT, and NEAR) to perform advanced searches. For more information, refer to Search Prefixes and Operators. This link takes you to a resource outside of AskF5, and it is possible that the document may be removed without our knowledge.
Start filtering your search with the Productfilter. You can select only one product at a time in the Productfilter. For example, if you want to view documents that apply to only the BIG-IP LTM system, select the check box next to BIG-IP LTM, and the results display only items that apply to the BIG-IP LTM system. Note that the name of the product you select appears at the top of the results list.
For example, if you select BIG-IP LTM in the Productfilter and 16.1.3 in the Versionfilter, the Content Type filter lists the different content types such as Supplemental Document, Operations Guideand Knowledgecontent types because, in this example, those are the only content types that include documentation that matches the search criteria you defined. You can further filter your search by selecting any of the listed Content Type items, and you see only documents of that particular content type in your results list.
Note: Boolean operators (AND, OR, NOT, and NEAR) are exceptions to this rule. You should enter these operators in all caps. For more information, refer to Search Prefixes and Operators. This link takes you to a resource outside of AskF5, and it is possible that the document may be removed without our knowledge.
Important: You must have the serial number or the last seven digits of the registration key to open a service case with F5 Support. If you cannot provide either, your technician may be able to locate your system in the support entitlement database.
The serial number format is F5-XXXX-XXXX. The serial number begins with F5, followed by a dash character ( - ), followed by four alphanumeric characters, followed by a dash, followed by four alphanumeric characters.
A BIG-IP Virtual Edition (VE) system does not have a similar serial number format to the previously mentioned hardware platforms. If you encounter any issue that requires F5 Support assistance, you cannot use the BIG-IP VE serial number to open a support case. You must use the last seven digits of the BIG-IP VE registration key.
You can get the serial number of a BIG-IP platform or BIG-IP VE by polling the F5 BIG-IP-system management information base (MIB) object identifier (OID):sysGeneralChassisSerialNum or its numeric equivalent, .1.3.6.1.4.1.3375.2.1.3.3.3.0.
If the license has not yet been activated on your BIG-IP LTM, BIG-IP DNS, BIG-IP APM, BIG-IP ASM, BIG-IP PSM, or WebAccelerator system, you can find the registration key in the /config/RegKey.license file. This file is present only on factory-installed systems.
Note: F5 sends registration keys for Return Materials Authorization (RMA) devices in an email. For more information about the F5"s RMA process, refer to K12882: Overview of the F5 RMA process.
You can obtain additional license information, including whether your devices are covered under an active support contract, from the F5 Licensing Tools page. To do so perform the following procedure:
CR135394NoneThe new APM iRule command, called ACCESS::session exists, can be invoked in events such as HTTP_REQUEST, to check whether the entry in the table is still valid. The iRule is documented on devcentral.f5.com.
CR135877NoneNew APM iRule ACCESS::uuid getsid commands enumerate the session IDs that belongs to a specified uuid key by the order of its creation and provides them in a Tcl list. Documentation is available on devcentral.f5.com.
IMPORTANT: The FDB table is managed by the system, and manual configuration requires intricate knowledge of the hardware data path. You should configure an FDB object only under the guidance of F5 Technical Support. Manually configuring FDB objects can potentially impact the flow of network traffic through the system.
description: The delay used by STP bridges to transition root and designated ports to forwarding. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)) F5 recommends keeping the default value. The range is from 4 to 30 seconds.
description: The interval between periodic transmissions of configuration messages by designated ports. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 1 to 10 seconds.
description: The maximum age of the information transmitted by the bridge when it is the root bridge. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 6 to 40 seconds.
description: The max hop determines the number of bridges in an MST region that a BPDU can traverse before it is discarded. F5 recommends keeping the default value. The range is from 1 to 255 hops.
description: The manageable component of the Bridge Identifier. F5 recommends configuring bridge-priority to a high value so that this device does not become the root bridge.
description: The manageable component of the Bridge Identifier. F5 recommends configuring bridge-priority to a high value so that this device does not become the root bridge.
description: The delay used by STP bridges to transition root and designated ports to forwarding. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 4 to 30 seconds.
description: The interval between periodic transmissions of configuration messages by designated ports. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 1 to 10 seconds.
description: The maximum age of the information transmitted by the bridge when it is the root bridge. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 6 to 40 seconds.
description: The manageable component of the Bridge Identifier. F5 recommends configuring bridge-priority to a high value so that this device does not become the root bridge.
description: The delay used by STP bridges to transition root and designated ports to forwarding. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 4 to 30 seconds.
description: The interval between periodic transmissions of configuration messages by designated ports. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 1 to 10 seconds.
description: The maximum age of the information transmitted by the bridge when it is the root bridge. Must follow restriction ((2 _ hello-time + 1) <= max-age) AND (max-age <= 2 _ (forwarding-delay - 1)). F5 recommends keeping the default value. The range is from 6 to 40 seconds.
Specify a separate endpoint for authenticating and uploading QKView files to the iHealth service. The authserver config element enables you to specify an authentication server URL for the iHealth service. By default, authserver is set to the F5 iHealth authentication server https://api.f5.com/auth/pub/sso/login/ihealth-api.
Specify the iHealth service has a separate endpoint for authenticating and uploading QKView files. The server config element enables you to specify an upload server URL for the iHealth service. By default, the server is set to the F5 iHealth upload server https://ihealth-api.f5.com/qkview-analyzer/api/qkviews?visible_in_gui=True.
(
description: A 27-character string that informs the license server about which F5 products you are entitled to license. The base registration key is preinstalled on your system. If you do not already have a base registration key, you can obtain one from F5 Technical Support.
description: License information for the system. Before you use system licensing manual-install, you use system licensing get-dossier to get the system dossier text, and then activate the license at activate.f5.com.
Generate an encrypted system dossier that can be used for retrieving a license from the F5 license server. This is used to perform a manual license installation.
description: A 27-character string that informs the license server about which F5 products you are entitled to license. The base registration key is preinstalled on your system. If you do not already have a base registration key, you can obtain one from F5 Technical Support.
system-dossier 48d05131e8688755efde6b1081af5e190793e5a0cfb70cd2da9da8c4c9d9d412a6360a11b869f2dfc779ef7c91df246f7184fe0010b7bcbd420e1664cb1d13b9890ec812bedf05d8cd530c87t82d13a7b63b9823ebdafc5f9061d6c12eb09a5a973361681d31a07dc92d774345cc52e70f8026729df4e2b5c9e6c22f96764e1cdd402f9e499841253259122877a85d7145a658a8444b0b6bc2dc8b9ef4a0156b8af2baa14500e9ce8c3ebcdf4060b35e1748aee093f0bb2349f53bf72f94c61979d1b8ccaf01c84235acf025f3cb3cad3f2cac9938b7481635280cc1589fac997aa4f6db9e8e04d02af5d91f5cd570fc261612233a1204e27a0d2ffd62e4107f89ad286a42ae07cea0918a7be0ba50e307664f8aaf9334051abb6d1559771d2fbfeb8f67335a8325b63a00ddfed563a926d595f1fe049bedf418dd997120945b1d622a574bd957fe6c60924c5562e6cf8ba837124a16bd2a49d1af0ace1f9dbe02af626336e073e8a2802949812eb0227faed9ad787c945c486dbc6d45327688025bcac81e472f3720c615f52455c8e0b235262cb4c8f2dd1ef8c753966fe11798db01714fd95e11348e1036f1ff69da16342595650c91b771cf7a28970c3caffa988faaf8f01cbd846151cd17201c3c8e58b18587e52a8be18f2ac9f175a41296fe9de3532433e94817f9b08ab2d9f66cdb76506e7d4156f9eb8af96aee363e8ab18eec930f6cc1c2dc80e2b254fbc9e31851a10f34506d71e1e5d60344a1ed5ec021c0e63513fd833ea8286258f6094592c7d04f9d29db93114518024b9129acb36ce41b1d1c7405db549f3aaa697919592a6dabfece7295cf57d8b950fcfed6cc40286d830be12097b0e3c0f9acbc07ccdb110b3cc98ca5a1ac09d6b152b2ace004d613364242a031e21057d3dc270ba00fe6918b3075b4692f55ca71fe6cd76c91f4beb19af97bb47dd677a77159e78adfa7e7cf0feb8a3490fc59fe660b26eb5268ecfed6f03c41ea0edadc7bc7573e91d0ad01313ee07e8719ec4d59fd6c90fcdbd29407f0a7666ff9de33251b04e270eb2d46c6cf8583d163c47d5768
description: A 27-character string that informs the license server about which F5 products you are entitled to license. The base registration key is preinstalled on your system. If you do not already have a base registration key, you can obtain one from F5 Technical Support.
Configure whether the system locator function is enabled. Enabling this function illuminates the F5 logo ball so that you can more easily locate a chassis in a data center.
description: Selector facility or severity selector on which to filter messages. F5OS supports only the LOCAL0 logging facility. All logs are directed to this facility, and it is the only one that you can use for remote logging.
Configure an NTP server with the address time.f5net.com, where the association type is SERVER, iburst is enabled, port is 123, it is the preferred server, and version number is 4:
appliance-1(config)# tenants tenant bigip-vm config type BIG-IP image BIGIP-bigip15.1.0.123.ALL-F5OS.qcow2.zip.bundle nodes 1 port 22 mgmt-ip 192.0.2.71 netmask 255.255.255.0 gateway 192.0.2.254 vlans 100 running-state deployed
A vlan-listener is a system-generated object and should only be configured manually under the guidance of F5 Technical Support. Manually configuring a vlan-listener object could potentially impact the flow of network traffic through the system.
file transfer-operations transfer-operation images/tenant/BIGIP-15.1.4-0.0.10.ALL-F5OS.qcow2.zip.bundle spkapexsrvc01.olympus.f5net.com v15.1.4/daily/build10.0/VM/BIGIP-15.1.4-0.0.10.ALL-F5OS.qcow2.zip.bundle "Import file" "HTTPS "
Display whether the system locator function is enabled. This function illuminates the F5 logo ball so that you can more easily locate a chassis in a data center.
F5 solutions integrate with the leading private cloud technology stacks, including OpenStack, VMware, and Microsoft. For OpenStack, F5 provides native orchestration with Heat templates to automate the end-to-end deployment of advanced app and security services, reducing deployment times from days to minutes. Integration with VMware vRealize Orchestrator through the Blue Medora vRO plug-in reduces configuration time, enables selfservice of F5 application services by app owners, and automates complex, multi-step workflows. F5 iWorkflow enables integration of F5 devices with software-defined networking (SDN) orchestration systems providing a single point of contact between the orchestrator and F5 devices.
Tier 2—the tenant or app tier—includes emerging, cloud-native applications that can be hosted in containers or disaggregated into microservices. The apps require specific services addressing intra-app traffic (east-west traffic). Those services, which can include basic load balancing to web app firewall or web performance optimizations, can be delivered on a per-application basis through highly scalable, flexible software such as virtual editions of BIG-IP products. This two-tier architecture model, standardized on F5 application services, offers flexibility, a strategic point of control where proven app policies can be enforced, and complete visibility of all traffic, taking advantage of hardware where it’s needed and software agility near the app.
F5 Application Connector is an add-on to the F5 BIG-IP platform, allowing services insertion for public cloud applications. It also acts as a cloud proxy instance for securely connecting public clouds to an organization’s application service infrastructure within cloud interconnects (colocations) or data centers. This enables the use of public cloud resources as part of an organization’s compute infrastructure. Application Connector also performs workload discovery within the Amazon Web Services (AWS) and Azure public cloud, and provides a secure connection back to interconnect services or data centers, allowing application services insertion on the BIG-IP platform.
Enabling automation and orchestration is key to achieving the benefits of cloud and software-defined architectures and to scaling application services on demand. F5 platforms offers many ways to program the application services fabric and network, enabling organizations to automate deployment, react in real time to events, and easily integrate into orchestration systems. F5 iRules scripting has long provided granular traffic control and visibility, enabling customization, rapid response to code errors and security vulnerabilities, and support for new protocols. New F5 iRules LX lowers costs and speeds deployments by extending iRules to JavaScript developers and providing access to, and easier integration with, over 250,000 community Node.js packages. In addition, with F5 iApps templates, organizations can automate deployment and configuration of application services in minutes. F5 iControl® REST APIs and SDKs provide integration with leading open source and commercial orchestration systems, VMware, OpenStack clouds, and configuration management systems such as Puppet, Chef, and Ansible.
F5 BIG-IQ Centralized Management is F5’s management and orchestration platform. It provides a central point of control for F5 physical and virtual devices and the app delivery and security services that run on them. BIG-IQ Centralized Management is available both as a virtual edition and an F5 appliance. It simplifies management, helps ensure compliance, and gives you the visibility and reporting you need to troubleshoot and respond to issues and security attacks.
BIG-IQ Centralized Management manages policies, licenses, SSL certificates, images, and configurations for F5 devices and the following BIG-IP software modules:
BIG-IQ Centralized Management supports BIG-IP appliances, VIPRION chassis/blades, and BIG-IP virtual editions (VE), whether they are running locally or in the cloud. It is ideal for organizations that require central management of F5 devices and modules, license management of BIG-IP VEs, or central reporting and alerting on application availability, performance, and security.
BIG-IP iSeries appliances include a baseboard management controller (BMC) and support for the Intelligent Platform Management Interface (IPMI) protocol. With the BMC and Always-On Management (AOM) firmware, F5 customers can have deeper access to internal sensor data for system monitoring, including multiple thermal, airflow, and voltage readings. Out-of-band alerts for hardware-level problems are possible without a running TMOS instance. Gain remote system console access to the BMC and AOM functions through the same IP address of the TMOS management port, eliminating the need for a special or separate network. BIG-IP iSeries appliances also can show system information, such as sensor values for troubleshooting, on their color touchscreen LCD displays.
The Federal Information Processing Standards (FIPS) specify requirements for cryptographic modules. FIPS compliance is required for many government agencies and industries such as financial services and healthcare that demand the highest standards in information, application, and data security. F5 offers a broad range of FIPS-certified hardware appliances that support a FIPS 140-2 Level 2 implementation for RSA cryptographic key generation, use, and protection. Keys generated on or imported into a BIG-IP system hardware security module (HSM) are not extractable in plain-text format. BIG-IP hardware appliances with integrated HSMs also have tamper-evident seals with a hardened-epoxy cover that, if removed, will render the card useless. For additional protection, the BIG-IP 10350v-F supports a FIPS 140-2 Level 3 implementation of the Internal HSM (PCI card). This security rating means the 10350v-F HSM card adds tamper-resistance, which is an additional means of detection to the tamper-evident methods of Level 2, as well as a response to physical access attempts, or to cryptographic module use or tampering.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey