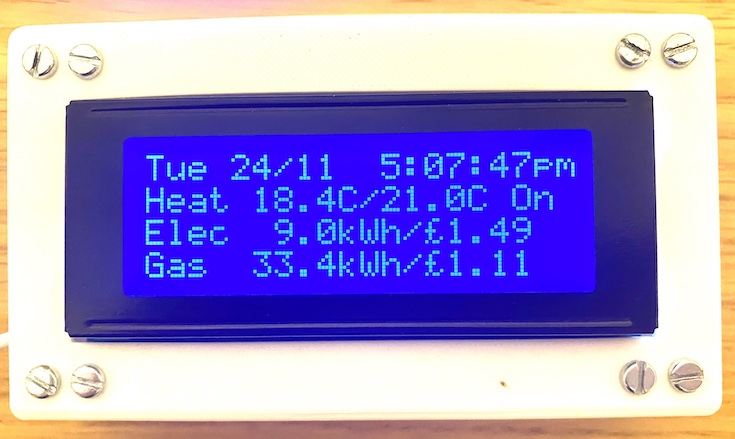
linux lcd panel info made in china

Check the number in the table, this is your address. If there are more devices on your I2c bus, there will be several addresses visible. To be sure, unplug all other devices and the address left will be the LCD (or try them all)

BEIJING (Reuters) - Two new Chinese LCD screens in Beijing’s imposing Great Hall of the People will replace screens made by a Japanese competitor, in a sign of resolve to supply the world with Chinese brands and not just Made in China products.Delegates arrive for the National People"s Congress (NPC), China"s annual parliament, in the Great Hall of the People in Beijing March 9, 2012. REUTERS/David Gray
The screens are made by Chinese electronics giant TCL. At 110 inches, they are the world’s largest high-definition 3-D LCD screens, just a touch wider than the 108-inch Panasonic models they will replace.
“We have broken through the Japanese and South Korean monopoly of big flat-screen TVs!” TCL chairman Li Dongsheng boasted at a launch ceremony on Friday. Officials from the Ministry of Commerce, Ministry of Science and Technology, Ministry of Industry and Information Technology (MIIT), and the government of Shenzhen, TCL’s hometown, clapped and nodded.

BEIJING (Reuters) - A joint venture between Hon Hai Precision Industry Co, known as Foxconn, and Sharp Corpplans to build a 61 billion yuan ($8.8 billion) factory in China to produce liquid-crystal displays (LCDs).
Sakai Display Products Corp’s plant will be a so-called Gen-10.5 facility specializing in large-screen LCDs and will be operational by 2019, the company said at a signing event with local officials in Guangzhou on Friday. It said the plant will have capacity equating to 92 billion yuan a year.
Global LCD output was hit this year by the closure of a Samsungfactory that accounted for 3 percent of the market, as well as factory stoppages in Taiwan after an earthquake in March.
China’s largest LCD panel maker, BOE Technology Group, began construction on its own Gen-10.5 plant in Hefei in December last year, with production scheduled to begin in 2018.
In May Shenzhen China Optoelectronics Technology Co, asubsidiary of TCL Corp, announced that it would begin construction on a 50 billion yuan LCD plant in Shenzhen.

Our company specializes in developing solutions that arerenowned across the globe and meet expectations of the most demanding customers. Orient Display can boast incredibly fast order processing - usually it takes us only 4-5 weeks to produce LCD panels and we do our best to deliver your custom display modules, touch screens or TFT and IPS LCD displays within 5-8 weeks. Thanks to being in the business for such a noteworthy period of time, experts working at our display store have gained valuable experience in the automotive, appliances, industrial, marine, medical and consumer electronics industries. We’ve been able to create top-notch, specialized factories that allow us to manufacture quality custom display solutions at attractive prices. Our products comply with standards such as ISO 9001, ISO 14001, QC 080000, ISO/TS 16949 and PPM Process Control. All of this makes us the finest display manufacturer in the market.
Choosing services offered by Orient Display equals a fair, side-by-side cooperation between the customer and our specialists. In each and every project, we strive to develop the most appropriate concepts and prototypes that allow us to seamlessly deliver satisfactory end-products. Forget about irritating employee turnover - with us, you will always work with a prepared expert informed about your needs.

According to "The Arch Way": We cannot configure everything for you, because "Preferences and needs are different for everyone", but we will try to ensure the configuration to be convenient and simple. In fact, it is even easier than some Chinese versions of Linux.
In Linux, locales are used to set up different environments for running programs. Commonly used Chinese locales are (the most intuitive is the number of words that can be displayed):
Warning: Globally setting Chinese locales in /etc/locale.conf will cause tty to display garbled texts due to the tty glyph limitation of Linux kernel. To properly display Chinese characters under tty, install and configure AUR.
Reason: The ~/.fonts path is deprecated. It may be preferable to link to Fonts#Manual installation instead of duplicating information regarding font paths here. (Discuss in Talk:Localization/Simplified Chinese)
However, the downloaded file name is still garbled and needs to be patched and compiled. The patch address is: https://www.teatime.com.tw/%7Etommy/linux/gftp_remote_charsets.patch

the Linux diagnostic extension helps a user monitor the health of a Linux VM running on Microsoft Azure. It has the following collection and capabilities:
You can enable this extension for your VM and virtual machine scale set by using the Azure PowerShell cmdlets, Azure CLI scripts, Azure Resource Manager templates (ARM templates), or the Azure portal. For more information, see Extensions and features.
Some components of the Linux Diagnostic VM extension are also shipped in the Log Analytics VM extension. Because of this architecture, conflicts can arise if both extensions are instantiated in the same ARM template.
The Linux diagnostic extension supports many distributions and versions. The following list of distributions and versions applies only to Azure-endorsed Linux vendor images. The extension generally doesn"t support third-party BYOL and BYOS images, like appliances.
Azure Linux agent version 2.2.0 or later. Most Azure VM Linux gallery images include version 2.2.7 or later. Run /usr/sbin/waagent -version to confirm the version installed on the VM. If the VM is running an older version of the guest agent, update the Linux agent.
We are currently planning to converge all versions of the Linux Diagnostic Extensions (LAD) with the new Azure Monitoring Agent - which already supports Python 3. We expect to ship this early to mid 2022; after which the LAD will be scheduled for deprecation pending announcement and approval.
If your protected settings are in the file ProtectedSettings.json and your public configuration information is in PublicSettings.json, run this command:
az vm extension set --publisher Microsoft.Azure.Diagnostics --name LinuxDiagnostic --version 4.0 --resource-group
If your protected settings are in the $protectedSettings variable and your public configuration information is in the $publicSettings variable, run this command:
Set-AzVMExtension -ResourceGroupName
az vm extension set --publisher Microsoft.Azure.Diagnostics --name LinuxDiagnostic --version 4.0 --resource-group
Set-AzVMExtension -ResourceGroupName
wget https://raw.githubusercontent.com/Azure/azure-linux-extensions/master/Diagnostic/tests/lad_2_3_compatible_portal_pub_settings.json -O portal_public_settings.json
az vm extension set --publisher Microsoft.Azure.Diagnostics --name LinuxDiagnostic --version 4.0 --resource-group $my_resource_group --vm-name $my_linux_vm --protected-settings "${my_lad_protected_settings}" --settings portal_public_settings.json
$publicSettings = (Invoke-WebRequest -Uri https://raw.githubusercontent.com/Azure/azure-linux-extensions/master/Diagnostic/tests/lad_2_3_compatible_portal_pub_settings.json).Content
Set-AzVMExtension -ResourceGroupName $VMresourceGroup -VMName $vmName -Location $vm.Location -ExtensionType LinuxDiagnostic -Publisher Microsoft.Azure.Diagnostics -Name LinuxDiagnostic -SettingString $publicSettings -ProtectedSettingString $protectedSettings -TypeHandlerVersion 4.0
wget https://raw.githubusercontent.com/Azure/azure-linux-extensions/master/Diagnostic/tests/lad_2_3_compatible_portal_pub_settings.json -O portal_public_settings.json
az vmss extension set --publisher Microsoft.Azure.Diagnostics --name LinuxDiagnostic --version 4.0 --resource-group $my_resource_group --vmss-name $my_linux_vmss --protected-settings "${my_lad_protected_settings}" --settings portal_public_settings.json
This set of configuration information contains sensitive information that should be protected from public view. It contains, for example, storage credentials. The settings are transmitted to and stored by the extension in encrypted form.
The sinksConfig optional section defines more destinations to which the extension will send collected information. The "sink" array contains an object for each additional data sink. The "type" attribute determines the other attributes in the object.
The public settings structure contains various blocks of settings that control the information that the extension collects. Each setting, except ladCfg, is optional. If you specify metric or syslog collection in ladCfg, you must also specify StorageAccount. You must specify the sinksConfig element to enable the Azure Monitor sink for metrics from LAD 4.0.
(Optional) A comma-separated list of names of sinks to which LAD sends aggregated metric results. All aggregated metrics are published to each listed sink. Example: "MyEventHubSink, MyJsonSink, MyAzMonSink". For more information, see sinksConfig (protected settings) and sinksConfig (public settings).
Note: if viewing the same metric in the azure.vm.linux.guestmetrics Metrics Namespace (available if AzMonSink is configured) the display name depends entirely on the counter. See the tables below to find the mapping between counters and names.
A syslog severity level, such as "LOG\_ERR" or "LOG\_INFO". For more information, see the "level" section of the syslog man page. The extension captures events sent to the facility at or above the specified level.
Due to implementation details, the metric values between Guest (classic) and azure.vm.linux.guestmetrics versions will differ. While the classic metrics had certain aggregations applied in the agent, the new metrics are unaggregated counters, giving customers the flexibility to aggregate as desired at viewing/alerting time.
The Processor class of metrics provides information about processor usage in the VM. When percentages are aggregated, the result is the average across all CPUs.
The File system class of metrics provides information about file system usage. Absolute and percentage values are reported as they would be displayed to an ordinary user (not root).
What do you do? You kill the process. But how? Believe it or not, your best bet most often lies within the command line. Thankfully, Linux has every tool necessary to empower you, the user, to kill an errant process. However, before you immediately launch that command to kill the process, you first have to know what the process is. How do you take care of this layered task? It’s actually quite simple…once you know the tools at your disposal.
The steps I’m going to outline will work on almost every Linux distribution, whether it is a desktop or a server. I will be dealing strictly with the command line, so open up your terminal and prepare to type.
From this list you will see some rather important information. Say, for example, Chrome has become unresponsive. According to our top display, we can discern there are four instances of chrome running with Process IDs (PID) 3827, 3919, 10764, and 11679. This information will be important to have with one particular method of killing the process.
Although top is incredibly handy, it’s not always the most efficient means of getting the information you need. Let’s say you know the Chrome process is what you need to kill, and you don’t want to have to glance through the real-time information offered by top. For that, you can make use of the pscommand and filter the output through grep. The ps command reports a snapshot of a current process and grepprints lines matching a pattern. The reason why we filter ps through grep is simple: If you issue the ps command by itself, you will get a snapshot listing of all current processes. We only want the listing associated with Chrome. So this command would look like:
When you issue the command above, you’ll be given more information than you need (Figure 2) for the killing of a process, but it is sometimes more efficient than using top.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey