hacking lcd displays made in china

I am aware that there are better alternatives for screens that can be found for under £15. I was curious what was in a £15 quid projector and bought it for that reason. Disassembling it was fun and has already netted me lenses, heatsinks, and LEDs etc. for other projects which is worth more than its cost. The reason I asked was because a) I am loathe to bin the LCD and hence contribute to our electronic waste problems, and b) I am specifically looking for LEDs (most of the displays on eBay and Amazon are OLEDs) as I want to make an ESP32-controlled projector as a project. Non-OLEDs are difficult to find on eBay/Amazon nowadays. Hence I was asking on the off-chance that this screen might be similar to something else in Occidental part of the world that I could use.
From what you say it feels its very unlikely for there to be a shortcut and I"ll have decode the signals manually. Designing and manufacturing (or finding a 30 pin adapter) is not a problem but I can"t justify to myself spending the better part of my weekends in a month to decode the signals just to use it when I can spend £10 buying an SPI LCD from eBay which does the exact same thing. I"ll probably bite the bullet and do that.
Shame about having to bin the screen though. I have found the schematics for the GM8284DD chip and probably with a magnifying glass would be able to make out the LCD connections (RGB input etc.) on the circuit board but again, I"m not sure if its that cost-efficient spending that many weekends working on it...

Feb 28 (Reuters) - Security researchers with U.S. cybersecurity firm Symantec said they have discovered a “highly sophisticated” Chinese hacking tool that has been able to escape public attention for more than a decade.
The Chinese embassy in Washington did not respond to a request for comment. Chinese officials have previously said China is also a victim of hacking and opposes all forms of cyber attacks.

Those are not even the worse “hardware trojans”. consider, contraband computer monitors with the hidden “wifi direct” interface built into LCD graphics chip. If you want to spy on what people are doing in a department. you just upgrade their computer monitors that can be secretly turned on like multichannel DVR security system. Or how about the USB thumb drive with the passive RF backdoor… even if you USB thumb drive is not plugged in… they can still scan every usb drive in a given area by sending out RFID signals to power the trojan circuit to readout the cache of the last thing you saved to the USB thumb drive and report it back to the secret basestation hidden in a place like a super market or department store. and the worse of the worse… the implantable “RF microdots” … you don’t need an ear piece to listen to your cellphone or mp3 player… or even a large hearing aid to hear… al you need is an “RF microdot” injected into the inner ear on both sides of your head… except its never used for anything useful like that… its used to screw around with people in stereo sound… a simple 10 minute procedure… drug victim… inject “RF microdots” … and install RF basestation near by… its as easy as that
Those are not even the worse hardware trojans””. consider”””” contraband computer monitors with the hidden “”””wifi direct”””” interface built into LCD graphics chip. If you want to spy on what people are doing in a department. you just upgrade their computer monitors that can be secretly turned on like multichannel DVR security system. Or how about the USB thumb drive with the passive RF backdoor… even if you USB thumb drive is not plugged in… they can still scan every usb drive in a given area by sending out RFID signals to power the trojan circuit to readout the cache of the last thing you saved to the USB thumb drive and report it back to the secret basestation hidden in a place like a super market or department store. and the worse of the worse… the implantable “”””RF microdots”””” … you don’t need an ear piece to listen to your cellphone or mp3 player… or even a large hearing aid to hear… al you need is an “”””RF microdot”””” injected into the inner ear on both sides of your head… except its never used for anything useful like that… its used to screw around with people in stereo sound… a simple 10 minute procedure… drug victim… inject “”””RF microdots”””” … and install RF basestation near by… its as easy as that”””””””
Those are not even the worse “hardware trojans”. consider, contraband computer monitors with the hidden “wifi direct” interface built into LCD graphics chip. If you want to spy on what people are doing in a department. you just upgrade their computer monitors that can be secretly turned on like multichannel DVR security system. Or how about the USB thumb drive with the passive RF backdoor… even if you USB thumb drive is not plugged in… they can still scan every usb drive in a given area by sending out RFID signals to power the trojan circuit to readout the cache of the last thing you saved to the USB thumb drive and report it back to the secret basestation hidden in a place like a super market or department store. and the worse of the worse… the implantable “RF microdots” … you don’t need an ear piece to listen to your cellphone or mp3 player… or even a large hearing aid to hear… al you need is an “RF microdot” injected into the inner ear on both sides of your head… except its never used for anything useful like that… its used to screw around with people in stereo sound… a simple 10 minute procedure… drug victim… inject “RF microdots” … and install RF basestation near by… its as easy as that

Luckily, all the digital devices in his 2012 Hyundai Genesis Coupe were connected using a fairly common standard — the “Controller Area Network bus” (or CAN bus). So Harin grabbed one of his Arduino’s — plus a cheap SPI CANBUS circuit board — and just started doing some experiments. When he first installed his Arduino circuit board into the dashboard, the LCD began showing the time of day — every ten milliseconds — and any new messages that he sent to the screen were simply being wiped out when the system re-transmitted. But Harin had already built up a strong motivation to keep moving forward, according to a recent write-up in Make: magazine, because “I hated that stupid little blue LCD. It would just sit there staring at me brightly with the words ‘AUX’…”
So he re-routed the LCD’s input. And fortunately, Harin’s other Raspberry Pi board could accommodate a WiFi dongle. By using an iPhone for connectivity, it was now able to draw down the funny Reddit quotes. And Make: also reported that his next project may be to install a router directly into his car.
Harin’s even mounted his Nexus 7 Android tablet into his car’s dashboard and is using it to play music. In the comments on his blog, he talks about one day transmitting the “now playing” information from the tablet to the LCD. Somewhere in the mix, there’s even an SQL database. “My main script retrieves the top post from Shower Thoughts and converts the characters to their hexadecimal equivalents, adds the message ID and row identifier, and stores it in an SQL database.”
There’re two more scripts just for retrieving the quote from the database and display it on the screen, which Harin says will be building blocks for more features down the road. “Eventually, I’ll be able to screen the messages intended for the LCD on the primary [CAN bus] network and add the ones I want to keep to the SQL database while removing the ones I don’t need anymore.”

The United States has asked countries including China for help confronting North Korea, but the issue of hacking is a sensitive one in Sino-US relations, with the two sides frequently trading accusations of cyber espionage.
A statement posted on China"s foreign ministry"s website on Monday noted that in the discussion of the hacking: "Wang Yi reiterated China"s relevant position, emphasising that China is against all forms of cyber attacks and cyber terrorism."
![]()
The first step in the hack is to select a compatible LCD that’s also conveniently available. For various reasons related to how the flat panel display market works, LCDs are difficult to purchase in their raw form. Fortunately, Mouser Electronics has a fair selection of LCD modules available and in-stock, although the price is no where near wholesale. I found that the Microtips MTF-TV57NP721-AV was a good match; you can buy these directly from Mouser for $150.80 by ordering part number 668-MTF-TV57NP721-AV. This LCD module uses a compatible signal format, has an LED backlight that works with a slightly modified chumby backlight driver, and also features a 4-wire resistive touchscreen, which is exactly the technology used by the stock chumby device. While the datasheet for this display is not available for convenient download, the datasheet itself is not marked proprietary or confidential, so I was able to secure a copy with a phone call to the local Microtips sales representative.
The next step is to build an adapter board between the chumby and the LCD. The adapter board is necessary because the flat-flex connector used by the Microtips LCD has a different size and pinout from the existing chumby LCD connector. The design of the board doesn’t require many components, as it is just rewiring the signals between two connector formats, but getting the design right does require attention to detail. It’s particularly important to make sure you get the location of the connectors right, so as to minimize the stress on the flex cables, and you need to be aware of the pinout inversion that happens between the two sides of a flex cable mating to the same type of connector: pin 1 goes to pin 50, and vice versa. Here is a link to the schematic for the adapter board, and a link to the gerbers.
Since you won’t need the old LCD anymore, loosen the two long Philips screws on the wifi riser assembly and liberate the core from the LCD/bezel assembly by detaching the two flat flex cables that connect to the core board. Save the wifi riser assembly, screws, standoffs and cables. Also leave all the thermal pads in place; they will hold on their own if you do not peel them off of the circuit boards.
You will need to do some minor rework to the core circuit board of the chumby in order to beef up the backlight driver to work with the more power-hungry backlight of the larger LCD. The original chumby backlight is a 10.2 volt, 40 mA 3-LED backlight. The backlight inside the Microtips LCD is also a 10.2 volt backlight, but it requires 200 mA. Fortunately, the boost converter used to drive the chumby’s backlight has a current switch capable of handling that magnitude of current—the TPS65101 has a 2.3A switch in it. However, some of the external circuitry has to be upgraded. In particular, the catch diode D502 has a forward current rating of 0.5A. While the LCD only draws 200 mA, it is a boost converter so the amount of current going through the catch diode is going to be a bit bigger than the ratio of the output voltage to the input voltage times the average current. Therefore, D502 has to get an upgrade to a footprint-compatible but higher current version, such as the 1A-rated MBRX130TP by Micro Commercial, or the 1.5A-rated RB070M-30TR by Rohm. Finally, in order to actually increase the amount of current pumped into the LCD, the current sense resistor in the feedback network of the boost regulator has to be modified. R524 programs the backlight current in the “on” state of the backlight, though the following relationship: I = 1.146V / R524. Its stock value of 57.6 ohms yields a current near 20 mA; replacing this with a 5.6 ohm resistor will yield a current just over 200 mA.
Now that you’ve got all the bits and pieces, it’s time to put it all together. It’s good practice to mount the pieces so that they aren’t “floating”; the flat flex cables are fragile, and they will easily strain and break if you move the unit around too much. If you have access to a laser cutter, you can build the LCD mount using the designs presented below.
Next, cut a second protective bezel using 1/16” clear acrylic using the reverse bezel pattern. This pattern also has alignment markers on it, which are important for making sure the LCD’s active area is centered in the opening of the bezel. There is no need to treat the reverse bezel with paint because it is simply a protective layer to protect the painted front bezel from chipping and scratching.
A set of gaskets are applied to the outside of the LCD along the silvery circuitry area of the touchscreen panel in order to improve the touchscreen’s robustness against heat warpage of the acrylic that can cause the bezel to inadvertently touch down onto the screen. The gasket material in this case is Poron, but you may also use a couple layers of thin-cut pieces of masking tape to create a small offset between the bezel edge and the display.
Before screwing the backplate in place, attach the 33-pin flat flex cable (that you previously made by cutting down the 36-pin cable), and connect the other side to the adapter board; at this time, also connect the 4-pin touchpanel cable and the 50-pin cable for the LCD signals to the motherboard. Then, fold the adapter board assembly over and screw it in place using 4x M2x6mm socket cap screws.
You’re almost done! Flip the LCD assembly into the bezel, using the alignment pattern on the bezel as a guide, and glue the four LCD mounting corners in place, paying attention to ensure that the holes on the mounting corners line up with the holes on the back plate (you can accidentally put a mounting corner on upside down and have the holes end up on the wrong edge of the LCD). Standard super glue works well for this application. Allow the glue to dry for at least a half hour before proceeding.
The kernel contains the code that initializes the video frame buffer’s size, so the timing needs to be programmed into these registers by modifying the kernel source. Here is a patchfile that you can apply to the 1.5.0 kernel (build 565) that performs the appropriate initializations. The patch modifies one of the clock registers inside the MX21 to increase the frequency of the clock feeding the LCD controller, and it also modifies the LCD controller registers itself. It also patches code that handles copying the initial logo screen from a staging area in RAM to its final location. It’s more involved to get the bootloader to behave properly and show a more elegant startup screen; here is a link to the modified bootloader source. This code replicates the QVGA bitmaps stored in the bootloader four times over inside the VGA frame buffer for the chumby, and it handles some other corner cases during the hand-off between the bootloader and the kernel at higher resolutions as well.
Finally, reboot while holding down the touchscreen so that you enter the “Special Options” mode. When the selection screen comes up, you should be able to log in via the serial console and execute the command “update.sh USB”, which will overwrite the bootloader and the primary kernel with the code patches mentioned above. For safety reasons, the backup partitions’ kernel is not modified by the dongle, so you always have a safe partition to return to for re-flashing a broken chumby. The graphics on the screen will look funny in this mode, but it’s not harmful for the LCD.

Researchers at other security research groups, like Citizen Lab, had previously uncovered various pieces of China’s mobile hacking campaign and linked them back to Chinese state hackers. However, Lookout’s new report appears to be the first time researchers were able to piece these older campaigns with new mobile malware and tie them to the same groups.

US cyber-security firm FireEye has denied claims that have been ramping up on social media all last week about illegally "hacking back" a Chinese nation-state cyber-espionage group.
At the time, the report was a landmark moment in the cyber intelligence community, as it exposed the activities of Chinese hackers in a depth of details like never before, even going as far as pinning the hacking on Unit 61398 of China"s People Liberation Army (PLA), an attribution level unheard at the time.
But according to Sanger"s book, FireEye might have obtained all these details while "hacking back," a term used to describe the practice of using offensive hacking techniques to breach an attacker"s systems to determine his identity, what he stole, and even destroy some of the stolen data in order to protect the victim. The technique is illegal, under the terms of US law, and limited to approved US military personnel only.
One day I sat next to some of Mandia"s team, watching the Unit 61938 hacking corps at work; it was a remarkable sight. My previous mental image of PLA officers was a bunch of stiff old generals sitting around in uniforms with epaulets, reminiscing about the glory days with Mao. But these guys were wearing leather jackets or just undershirts, and probably saw Mao only if they visited his mausoleum in Tiananmen Square. "They were such bros," Andrew Scwartz, one of Mandia"s communications specialists, recalled later.
FireEye says Sanger never observed real-time hacking, but only pre-recorded videos of APT1 (PLA Unit 61398) operators interacting with computers on the network of compromised companies.
Furthermore, FireEye says it obtained permission from these companies to leave the compromised PCs intact and observe what the hackers were doing, and that at no point its employees used offensive hacking techniques.
Specifically, Mr. Sanger suggests our "…investigators reached back through the network to activate the cameras on the hackers" own laptops." We did not do this, nor have we ever done this. To state this unequivocally, Mandiant did not employ "hack back" techniques as part of our investigation of APT1, does not "hack back" in our incident response practice, and does not endorse the practice of "hacking back."
To someone observing this video "over the shoulder" of one of our investigators, it could appear as live system monitoring. Nevertheless, Mandiant did not create these videos through "hacking back" or any hacking activity. All of these videos were made through information obtained via consensual security monitoring on behalf of victim companies that were compromised.
But FireEye"s explanation also holds water, as it"s easy to misinterpret an RDP session for a live hacking op, especially if you"re not told what you"re watching. Although, one minor detail remains unaccounted for...

In an e-mail, Chinese embassy in the US spokesman Liu Pengyu (劉鵬宇) said officials in Beijing “firmly oppose and crack down on all forms of cyber hacking in accordance with the law” and that the US “has been loudly active in fabricating and spreading lies about so-called ‘Chinese hackers.’”
China shot back at accusations by the US and its allies that Beijing was behind a series of ransomware attacks and the hacking of Microsoft’s email server this spring, dismissing the charge as “made up out of thin air” and claiming that America “is the world champion of malicious cyber attacks.”
He went on to accuse the CIA of hacking China’s aerospace research facilities, oil industry, internet companies and government agencies in attacks that “severely compromised” national security.

President Barack Obama, in an end-of-year press speech on December 19, commented on the Sony hacking and stated that he felt Sony made a mistake in pulling the film, and that producers should "not get into a pattern where you are intimidated by these acts".Michael Lynton said on the CNN program
U.S. government officials stated on December 17, 2014 their belief that the North Korean government was "centrally involved" in the hacking, although there was initially some debate within the White House whether or not to make this finding public.Federal Bureau of Investigation (FBI) formally stated on December 19 that they connected the North Korean government to the cyber-attacks.malicious hacking tools and techniques previously employed by North Korean hackers—including North Korea"s cyberwarfare agency Bureau 121 on South Korean targets.
The North Korean news agency KCNA denied the "wild rumours" of North Korean involvement, but said that "The hacking into the SONY Pictures might be a righteous deed of the supporters and sympathizers with the DPRK in response to its appeal."
On the day following the FBI"s accusation of North Korea"s involvement, the FBI received an email purportedly from the hacking group, linking to a YouTube video entitled "you are an idiot!", apparently mocking the organization.
In China, the media coverage of the hackings has been limited and outside sources have been censored. A search for "North Korea hack" on Baidu, China"s leading search engine returned just one article, which named North Korea as "one of several suspects." However, Google, which was and is inaccessible in China, returned more than 36 million results for the same query.
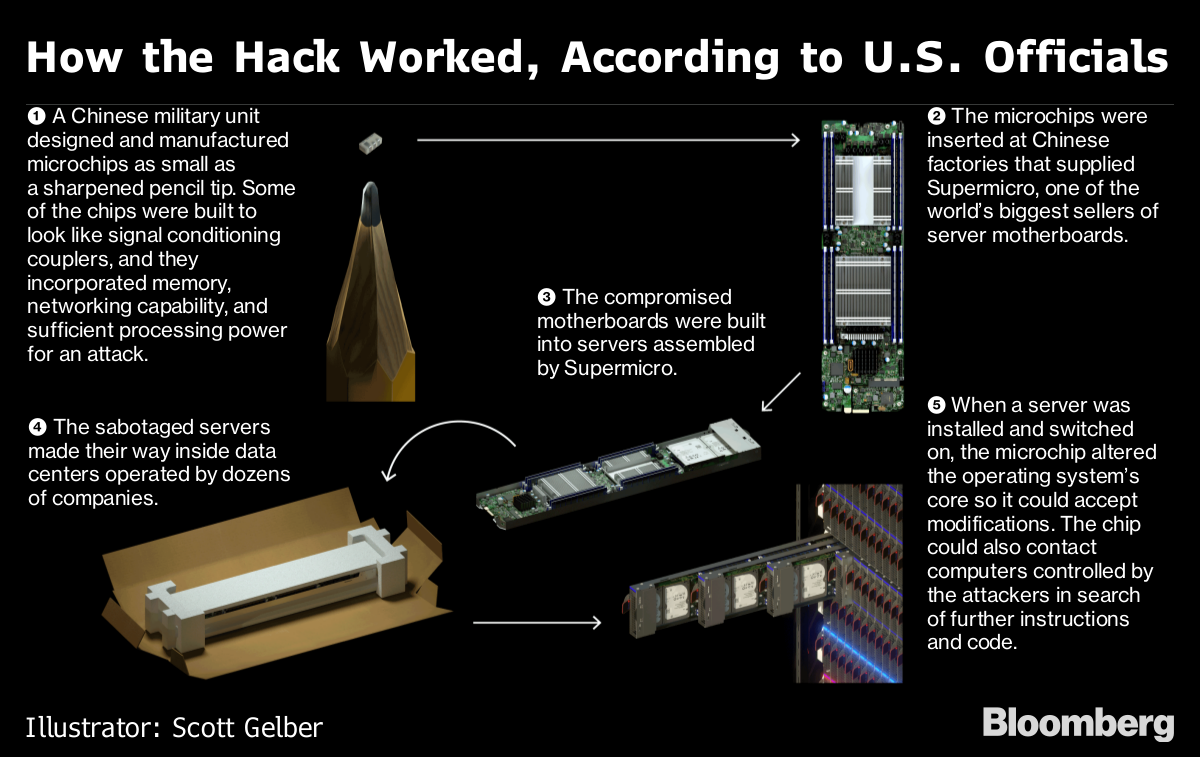
Not to be outdone, China made headlines, after the US indicted members of China’s elite hacking group APT10 with a massive campaign to infiltrate the IT infrastructure of the world. It also came out that China likely is behind the hack of diplomatic cables from the European Union, among other sensitive diplomatic communications. Despite all this, one China expert argued in an op-ed in WIRED Opinion that the US must engage China in tech.

Yet digital displays of information are better than old-fashioned alternatives because they can update in real time via the internet. Laptops can display digital information, but the light from their backlit screens is too obtrusive. So a hacker in the United Kingdom made himself a digital display which read by a room’s other light sources.
A quick word about e-paper: most consumers think a screen is a screen is a screen, but this is not true. The LCD screens on your mobile phone work by shining light out from behind it, changing the light’s color with embedded crystals. E-paper is read by the light that bounces off the screen, like paper. Turn the lights off, and you can’t see it.
These properties are why e-paper screens make for nice reading experiences, but it is surprising how under-utilized they have been for public displays. That is slowly starting to change. E-ink, the leading e-paper company, has been pitching its products more and more for retail displays and signage, but those uses are not yet widespread. Displio has a tiny version, but it isn’t shipping yet.
Fandos didn’t want to wait. He liked what Jeroen Domburg had done hacking an e-reader, but it looked like too much bother. “It involved designing my own board, buying components, soldering them (they are quite small) and testing the whole thing. It is hard to get that right on the first iteration,” he wrote. “So I went for an easier although more expensive approach: buy a random Chinese board that looked good and try to make sense of it.”
He shared his software so that others could make their own widgets using other sources. One can imagine a lot of consumer uses for non-obtrusive displays of information that can update from the internet. Sports scores for superfans. Transit times for commters. Observer headlines for everyone.

Security researchers with US cybersecurity firm Symantec said they have discovered a highly sophisticated Chinese hacking tool that has been able to escape public attention for more than a decade.
The Chinese embassy in Washington did not respond to a request for comment. Chinese officials have previously said China is also a victim of hacking and opposes all forms of cyberattacks.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey